- SHA1 packed: 4ad9a7f3a1d9e2549624c41e9a632d63a4e4b44e (Android.BankBot.250)
- SHA1 unpacked: a8b6f23d881bd30383ca31a8ae1175ee70b9e4be
A banking Trojan for Android mobile devices. It is designed to steal money from Sberbank’s Russian-speaking clients. It is distributed via fraudulent text messages that invite the potential victims to follow the link and supposedly become familiar with the reply to the posted ad or with the information on a loan or a money transfer. Android.BankBot.358.origin is installed on smartphones and tablets as programs of Avito, Visa, Western Union and other popular applications.
When launched, the Trojan attempts to get administrative privileges of the mobile device. For this purpose, it displays a dialog in an infinite loop and forces user to provide the required privileges. Then Android.BankBot.358.origin displays a fake message about an installation error and deletes its icon from the list of programs on the home screen, thus hiding its presence in the system.
If an owner of an infected smartphone or tablet tries to recall administrator privileges from the Trojan, Android.BankBot.358.origin prevents it by closing the settings window. Some Trojan modifications also install their own lock screen PIN codes.
Control of the infected devices is implemented via HTTP and GCM (Google Cloud Messaging). It is performed in the administration panel.
After a successful infection, Android.BankBot.358.origin sends to the command and control server a request register that contains the following information about a device:
json.put("sid", this.api_panel_id);
json.put("imei", this.getIMEI());
json.put("country", this.getCountry());
json.put("operator", this.getOperator());
json.put("phone", this.getPhone());
json.put("model", this.getModel());
json.put("version", this.getVersion());
json.put("application", this.context.getResources().getString(2131165185));
json.put("build", this.app_build);
json.put("process_list", process_list);
json.put("apps_list", apps_list);
json.put("method", "register");
The Trojan can execute the following commands:
- register_ok – receive interception templates for text messages and settings for blocking a screen with phishing windows;
- GCM_register_ok – confirmation of a successful sending of Google Cloud Message Key to the administration panel;
- START – launch the Trojan service;
- STOP – stop the Trojan service;
- RESTART – restart the Trojan service;
- URL – change the address of the command and control server;
- UPDATE_PATTERNS – update all data;
- UNBLOCK – recall the Trojan’s administrator rights;
- UPDATE – update the Trojan;
- CONTACTS – send SMS messages to all contact list numbers;
- CONTACTS_PRO – send SMS messages to all numbers specified in the command;
- PAGE – load a webpage with an address specified in the command;
- ALLMSG – send to the server all saved SMS messages from the device;
- ALLCONTACTS – obtain information on contacts from the contact list;
- ONLINE – check the Trojan’s status;
- NEWMSG – create a fake incoming SMS;
- CHANGE_GCM_ID – change GCM ID;
- BLOCKER_BANKING_START – block device’s screen with a fake mobile banking window;
- BLOCKER_EXTORTIONIST_START – block device’s screen with a ransom demand;
- BLOCKER_UPDATE_START – block device’s screen with a fake message about system update installation;
- BLOCKER_STOP – close a screen blocking message.
Depending on the response received from the server, the Trojan makes one of the following requests:
- "method", "message" – send an SMS from the Trojan’s SQLite database;
- "method", "gcm_register" – send a registry id GCM to the server;
- "method", "repeat" – a periodic check for new tasks;
- "method", "command_receive" – confirmation that a task has been received;
- "method", "save_contacts_list" – sending of information on contacts from the contact list;
- "method", "get_message_list" – request for a text of a message for mailing to contacts from the contact list;
- "method", "save_message_history" – forward all SMS messages saved on a device to the command and control server;
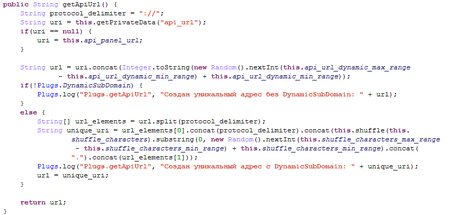
Each request is first encoded with Base64, then it is encrypted with the AES key and converted using the bytes to hex method. The obtained string is sent to the command and control server, which responds the same way with a string with the command. Additionally, the end path for connection with the server is generated randomly or the DynamicSubDomain method is used.
The data obtained by the Trojan and also device information are encrypted and stored in the local SQLite database. It has the following structure:
- init_imei;
- api_url;
- gcm;
- first_start;
- init_bootable;
- patterns;
- blocker_banking;
- blocker_banking_autolock;
- blocker_extortionist;
- blocker_extortionist_autolock;
- cardSuccess
- blocker_banking_success;
- immunity.
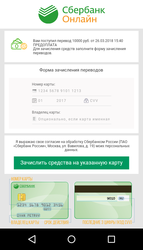
The main goal of Android.BankBot.358.origin is stealing money from the Sberbank’s clients. Cybercriminals send the Trojan a command to block an infected device with a phishing window. It imitates the appearance of Sberbank Online, the remote banking and payment system, and is displayed to all users no matter whether they are Sberbank or another financial organization’s clients. The user is offered to receive a money transfer the sum of which cybercriminals set via the administration panel. To receive the money, the user is invited to provide bank card information: its number, holder’s name, expiration date, and the CVV code. The fraudulent message cannot be closed, so a potential victim is actually forced to provide cybercriminals with the secret information.
If a user uses the Mobile banking service, Android.BankBot.358.origin tries to use it to steal money from the victim’s account. The Trojan sends SMS messages with commands to perform operations in the online banking system. It checks the current balance of the Android device owner’s card and automatically transfers money to the cybercriminals’ bank account, or to their mobile account.
Some versions of Android.BankBot.358.origin can block an infected device with a ransom message demanding that the victim pay a fine for watching prohibited videos. In order to hide their malicious activity, various Trojan’s modifications can also block the screen with a notification that some system update was installed.
News about the Trojan